The description of EAGLE Security UNLIMITED
Understanding Cell Phone Privacy Violations
In today's digital age, it's no secret that any cell phone can be wired, and phone numbers can be easily substituted. IMSI catchers are increasingly affordable and widely available devices that can facilitate these invasions of privacy. However, there are various methods through which your privacy can be compromised via cellular networks. Below, we explore three primary methods used to wiretap mobile phones.
1. Spyware (or Scumware)
Spyware is malicious software that can be installed on your mobile device, allowing it to:
- Record phone calls
- Capture photos and videos, even in standby mode
To protect yourself:
- Be cautious when installing new software.
- Check the app's permissions, especially for access to your camera, microphone, and sensitive data like calls and SMS.
- Research the producing company to ensure it is trustworthy.
Some spyware can be installed without your knowledge. These applications are often not available on Google Play and can only be installed from APK files. They may masquerade as legitimate apps with similar names and icons, such as Googel Services or Google Drlve. Be wary of package names that closely resemble popular applications, making them difficult to identify.
Individuals such as colleagues, relatives, or phone service technicians might install such spyware on your device.
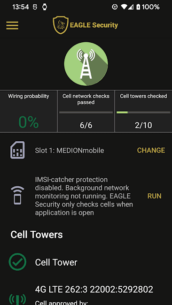
Eagle Security offers a solution by providing a comprehensive list of applications installed on your device. You can review the permissions requested by each app and identify those that may pose a risk to your privacy. Additionally, the app allows you to disable your camera and/or microphone, ensuring that no spyware can access them without your consent.
2. Substitution of Base Station
This method has gained popularity due to the affordability and accessibility of IMSI catchers. A wiring kit can be placed within a radius of 500 meters, causing nearby cell phones to connect to the fake station due to its strong signal. Often, IMSI catchers are used in conjunction with jamming stations to suppress legitimate cell towers, forcing nearby phones to register with the fake network.
These kits can be as small as an attache case and can operate without your knowledge. The substituted base station transmits all data to the real one, making calls appear normal. Such devices can be purchased at a low cost.
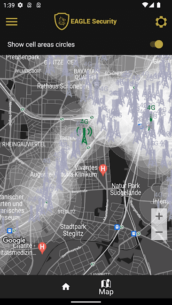
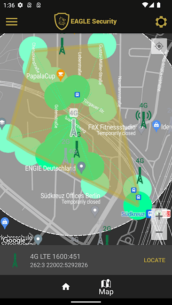
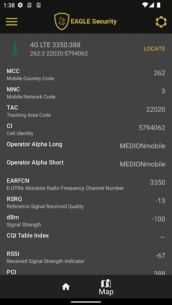
To protect yourself, consider tracking the stations your cell phone connects to. Eagle Security can check the signature of a station, as many tapping complexes have substandard signatures. It also monitors the locations of these stations. If a station appears in multiple locations or a new station appears near an existing one, it will be flagged as suspicious, alerting users who connect to it.
While connecting to a suspicious base station does not guarantee that someone is tapping your phone, it's advisable to avoid using your device in such situations.
3. Legal Wiretapping
In some cases, individuals with connections to security agencies can obtain official permission to wiretap a cell phone. In many countries, simply being a witness in a judicial case may suffice for such authorization. The targeted individual may remain completely unaware of the surveillance, as this type of tapping is often legally sanctioned.
To safeguard against this method, consider using voice and message encryption. Software from independent developers, such as Telegram, provides secure calling and messaging options.
Conclusion
Eagle Security empowers users to protect themselves effectively against the first two methods of privacy invasion discussed above. With this tool, you can monitor and explore the cellular network around you, as well as control application access to your device's hardware.
What's news
Changes are not available!
Download EAGLE Security UNLIMITED
Download the paid installation file with a direct link - 8 MB
.apk